SOC Visibility Triad is Now A Quad — SOC Visibility Quad 2025
SOC Visibility Triad is Now A Quad — SOC Visibility Quad 2025
I will be really, really honest with you — I have been totally “writer-blocked” (more “analyst blocked”, really) and I decided to release it anyway today … given the date. But I am taking a leap of faith here…
A bit of history first. So, my “SOC visibility triad” was released on August 4, 2015. It stated that to have good SOC visibility you need to monitor logs (L), endpoint (E) sources and network (N) sources. So, L+E+N was the original triad. Note that this covers monitoring mechanisms, not domains of security (more on this later; this matters!)
5 years later, in 2020, I revisited the triad, and after some agonizing thinking (shows at the above link), I kept it a triad. Not a quad, not a pentagram, not a freakin’ hex.
So, here in 2025, I am going to agonize much more .. and then make a call (hint: blog title has a spoiler!)
How do we change my triad?
First, should we …
… Cut Off a Leg?
Let’s look at whether the three original pillars should still be here in 2025. We are, of course, talking about endpoint visibility, network visibility and logs.

My 2020 analysis concluded that the triad is still very relevant, but potential for a fourth pillar is emerging. Before we commit to this possibly being a SOC visibility quad — that is, dangerously close to a quadrant — let’s check if any of the original pillars need to be removed.
Many organizations have evolved quite a bit since 2015 (duh!). At the same time, there are many organizations where IT processes seemingly have not evolved all that much since the 1990s (oops!).
First, I would venture a guess that, given that EDR business is booming, the endpoint visibility is still key to most security operations teams. A recent debate of Sysmon versus EDR is a reflection of that. Admittedly, EDR-centric SOCs peaked perhaps in 2020, and XDR fortunately died since that time, but endpoints still matter.
Similarly, while the importance of sniffing the traffic has been slowly decreasing due to encryption and bandwidth growth, cloud native environments and more distributed work, network monitoring (now officially called NDR) is still quite relevant at many companies. You may say that “tcpdump was created in 1988” and that “1980s are so over”, but people still sniff. Packets, that is.
The third pillar of the original triad — logs — needs no defense. Log analysis is very much a booming business and the arrival of modern IT infrastructure and practices, cloud DevOps and others have only bolstered the importance of logs (and of course their volume). A small nit appears here: are eBPF traces logs? Let’s defer this question, we don’t need this answer to reassert the dominance of logs for detection and response.
At this point, I consider the original three legs of a triad to be well defended. They are still relevant, even though it is very clear that for true cloud native environments, the role of E (endpoint) and N (network) has decreased in relative terms, while importance of logs increased (logs became more load bearing? Yes!)
Second, should we …
Add a Leg?
Now for the additions I’ve had a few recent discussions with people about this, and I’m happy to go through a few candidates.
Add Cloud Visibility?
First, let’s tackle cloud. There are some arguments that cloud represents a new visibility pillar. The arguments in favor include the fact that cloud environments are different and that cloud visibility is critical. However, to me, a strong counterpoint is that cloud visibility In many cases, is provided by endpoint, network, and logs, as well as a few things. We will touch these “few things” in a moment.
YES?
- Cloud native environments are different, they suppress E and N
- Cloud visibility is crucial
- Addresses unique cloud challenges
- Cloud context is different, even if E and N pillars are used for visibility
- CDR is a thing some say
NO?
- Cloud INCLUDES logs (lots, some say 3X in volume), and also E and N
- Too much overlap with other pillars (such as E and N)
- Cloud is a domain, not a mechanism for visibility.
- CDR is not a thing, perhaps
Verdict:
- NO, not a new pillar, part of triad already (via all other pillars)
Add Identity Visibility?
The second candidate to be added is, of course, identity. Here we have a much stronger case that identity needs to be added as a pillar. So perhaps we would have an endpoint, network, logs and identity as our model. Let’s review some pros and cons for identity as a visibility pillar.
YES?
- Identity is key in the cloud; we observe a lot of things via IDP … logs (wait.. we already have a pillar called “logs”)
- By making identity a dedicated pillar, organizations can ensure that it receives the attention
- ITDR is a thing
NO?
- But identify visibility is in the logs … we already have logs!
- Too much overlap with other pillars (such as logs and E as well)
- ITDR is kinda a thing, but it is also not a thing
Verdict:
- Sorry, still a NO, but a weak NO. Identity is critical as context for logs, endpoint data and network telemetry, but it is not (on its own) a visibility mechanism.
Still, I don’t want to say that identity is merely just about logs, because “baby … bathwater.” Some of the emerging ITDR solutions are not simply relying on logs. I don’t think that identity is necessarily a new pillar, but there are strong arguments that perhaps it should be…
What do you think — should identity be a new visibility pillar?
Add Application visibility?
Hold one, Anton, we need more data!
Here:

and

Now let’s tackle the final candidate, the one I considered in 2020 to be the fourth leg of a three legged stool. There is, of course, application visibility, powered by increased popularity of observability data, eBPF, etc. Application visibility is not really covered by endpoint orgs and definitely not by EDR observation. Similarly, application visibility is very hard to deduce from network traffic data.
YES?
- Application visibility is not covered by E and N well enough
- SaaS, cloud applications and — YES! — AI agents require deep application visibility.
- This enables deeper insights of the app guts, as well as business logic
NO?
- Is it just logs? Is it, though?
- Do organizations have to do application visibility (via ADR or whatever? Is this a MUST-HAVE but of 2030?
- Are many really ready for it in their SOCs?
Verdict:
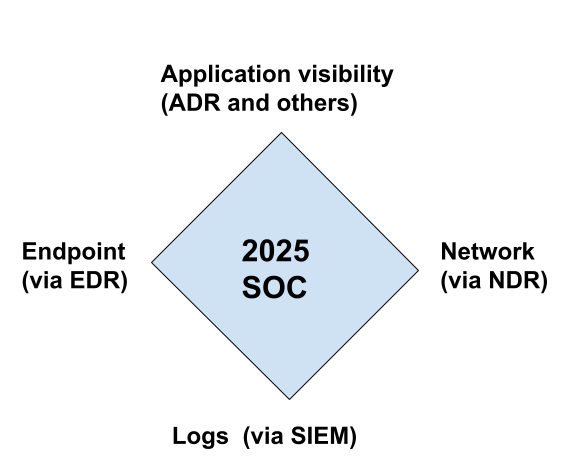
- YES! I think to have a good 2025 SOC you must have the 4th pillar of application visibility.
- And, yes, many are not ready for it yet, but this is coming…
So, we have a winner. Anton’s SOC visibility QUAD of 2025
- Logs
- Endpoint
- Network
- Application
Are you ready? … Ready or not, HERE WE GO!
Related blogs:
- WhatDR or What Detection Domain Needs Its Own Tools?
- Revisiting the SOC Triad 2020
- Baby ASO: A Minimal Viable Transformation for Your SOC
SOC Visibility Triad is Now A Quad — SOC Visibility Quad 2025 was originally published in Anton on Security on Medium, where people are continuing the conversation by highlighting and responding to this story.
The post SOC Visibility Triad is Now A Quad — SOC Visibility Quad 2025 appeared first on Security Boulevard.
>>More
